Social Engineering is a form of hacking that manipulates users online into divulging sensitive and private information in order to gain access to their computer system. The umbrella term can also include exploiting human vulnerability and biases, kindness, curiosity and greed to gain authorized access to restricted areas of buildings and a gateway to installing backdoor software on company computers.
Computer and Internet Security is tantamount to any company or individual operating online. Therefore knowing and understanding the tricks and tactics used by hackers is of the utmost importance to your Security Strategy.
In this article, we will discuss the common tricks used in Social Engineering and how you can devise security solutions to circumvent and counter these malicious actions by hackers.
We will outline the following:
- How Social Engineering Works
- Six Principles of Influence used by Social Engineering
- Common Social Engineering Tricks and Techniques
- Prevention: Social Engineering Counter Measures to Circumvent Hackers
Let’s dive right in.
Table of Contents
How Social Engineering Works
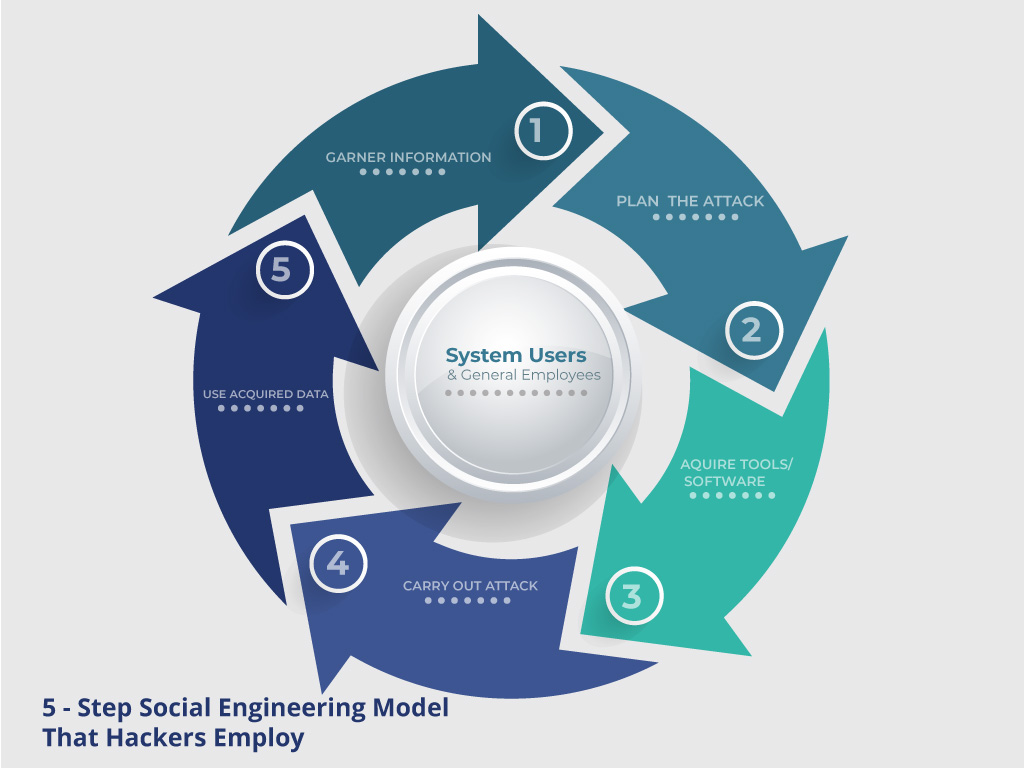
Hackers employ a 5 step system when using social engineering to effectively breach a security system and gain access to a company. Knowing the steps involved is the first step to identifying when you are under a social engineering attack.
Step 1: Gather Information
Before staging an attack a hacker has to learn his target inside and out so he is able to adequately exploit the target’s weaknesses. Information is gathered from a company’s website, directories, blogs, and other publications and to some degree, even calling to speak with employees to fish for information. The more information a hacker is able to gather the better he can launch his attack successfully.
Step 2: Plan the Attack
Once equipped with pertinent information the hacker can plan out his attack and how to execute it. The more information gathered the better the assault will be.
Step 3: Acquire Tools
Now that a plan is in place the hacker will acquire any tools necessary to launch the attack. These include any software, computer systems, or coding the hacker will need to breach security and execute the attack.
Step 4: Attack
The plan is now executed to exploit the weaknesses in the system and gain access.
Step 5: Use Gathered Knowledge
Once the attack is underway the hacker will use all the information gathered to help get beyond any other security measures. This involves using the information to guess passwords to gain access to restricted files for example.
The Six Principles of Influence used by Social Engineering Hackers
To understand the foundation of social engineering techniques you must first understand the human psyche. All Social Engineering techniques are based on the process of human decision making known as cognitive biases. These biases are mechanisms in the human psyche that are exploited during a social engineering attack.
Social Engineering is greatly dependent on 6 Principles of Influence established by Robert Cialdini. His theory of influence is based on these six principles.
1. Reciprocity:
People have a tendency of returning favours, thus why free sampling works so well in marketing campaigns.
2. Commitment and Consistency:
If people make a decision to commit, orally or in writing, to an idea or goal, they are more than likely to honour that commitment because of founding that idea or goal as being congruent with their self-image. Even though the original incentive or motivation is taken away after they have already decided, they will continue to honour the agreement.
3. Social Proof:
“Monkey see, Monkey do” an old American adage that exemplifies human behaviour. People will do things that they see other people doing, following the fashion so to speak. Conformity happens within social settings all the time.
4. Authority:
People will always bend to an authority, even if it goes against their personal and moral principles.
5. Liking:
People are easily influenced and persuaded by individuals they like. That’s why large brands and Corporations use well-loved celebrities as the image for their products. We’ve seen this now more than ever with Social Media Influencers becoming brand ambassadors to influence audiences to buy products.
6. Scarcity:
A founding principle in economics; alleged scarcity will always generate demand. That’s why marketers use it to drive sales by offering deals for a limited time only.
Social Engineering hackers use these six principles to target their intended victims effectively because human behaviour is so predictable.
Common Social Engineering Tricks, Tactics and Techniques
Social Engineering can take many forms in order to dupe people into giving up their confidential information. Some of the more common tricks and techniques used are as follows:
-
Exploiting Familiarity
In general, people are always more trusting and less suspicious of people they are familiar and friendly with. A hacker usually poses as someone that is trustworthy and friendly thus users let their guards down and interact with them willingly divulging information they wouldn’t otherwise divulge. An attacker can pose as an online friend, infiltrate the organization, present a very social and trusting front at Organizational Events, all in the efforts of getting users to let their guard down and not suspect them while gleaning information.
-
Vishing also referred to as “voice phishing”
Vishing is the criminal practice of using social engineering over the phone to gain access to confidential information that is personal and or financial. This is also used to gather more information to target a corporation or business for a larger attack later on. Hackers can call up a company member and pose in a myriad of ways in order to garner trust and then gather sensitive information.
-
Phishing
Phishing is a trick used by cyber criminals like hackers in order to gain personal information like passwords, account details and financial information. Usually, in a phishing scam, a hacker poses as a legitimate online business or company in order to get users to divulge sensitive details. Phishing scams have been used to steal credit card information, banking information, account information and much more from users.
-
Smishing
This is the fraudulent act of enticing victims into carrying out certain actions by way of SMS Texting. Just like phishing, it lures a victim into a trap of clicking a link to either install malicious backdoors or by having users enter personal information.
- Exploiting Human Curiosity
By nature people are curious. Hackers can exploit this facet of human behaviour by sending emails with infected files in order to insert viruses or backdoors on the computer system so that they can gain access. For example, impersonating another personnel’s email account and sending around a file called Employee Performance Report.doc. Once the user opens the file it infects the computer. These kinds of attacks can take any form. The key is tapping into human curiosity.
-
Exploiting Human Greed
Social Engineers can use the promise of financial gain to lure users into a trap to fill out a form with personal information like banking details.
Prevention: Social Engineering Counter Measures to circumvent Hackers
The majority of the tricks and tactics used by social engineers is founded on exploiting and manipulating human confirmation biases as stated earlier. To counter and circumvent these criminal techniques a Corporation or Individual can adopt the following measures:
-
To counter and Circumvent the Exploitation of Familiarity
Implement training sessions so that personnel recognise these situations even in the context of familiarity. Then, set mandates that ensures that familiarity is never a substitute for security. Even people that are familiar should always prove and authenticate their authorization to sensitive data or areas.
-
To counter and circumvent Phishing Techniques
Inform and educate users on how to spot a phishing scam. If hackers impersonate established companies like Google, Yahoo, or prominent banks they should be aware of SSL Certificates and secure connections. Major sites will always have SSL Encryption or https:// enabled in order to protect and encrypt sensitive data. Check the URL and ensure that it is secure before entering any confidential and financial information. Avoid or delete emails that demand you respond and provide personal details.
-
To counter and circumvent human curiosity
Sensitise employees or users of scams that prey to their curious nature. In addition, some form of Internet Security software must accompany each email to adequately filter suspicious emails and spam.
Conclusion
Social Engineering includes tactics and techniques used by cybercriminals that prey on human biases in order to manipulate them into divulging confidential information or duping them into installing malicious software onto computer systems. Ensure you put proper security measures in place as well as education on such techniques to prevent and circumvent such attacks.
